Online gambling account takeovers spike, so stop using lame passwords
Online gambling operators are increasingly being targeted for account takeover fraud, in part due to customers choosing some truly lousy passwords.
A new survey of global fraud and payments professionals by the Ravelin fraud detection firm found gambling second only to taxi companies in terms of the average annual number of account takeover attacks. These attacks involve fraudsters obtaining customer credentials to take control of an online account and then either use the account to spend lavishly on goods or services or sell the compromised data to nefarious third parties.
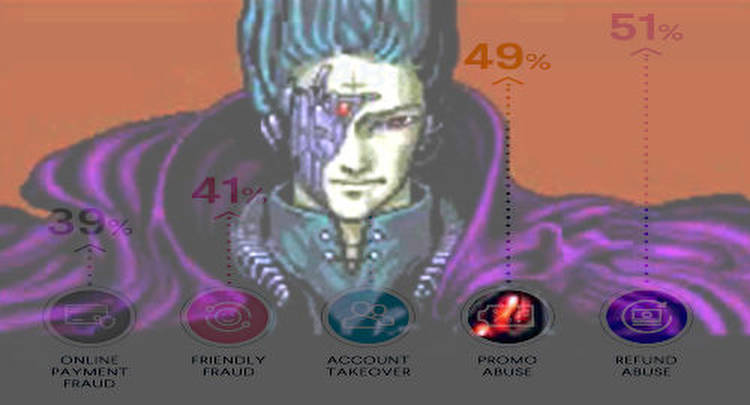
Gambling firms faced an average of 60 account takeover attacks per year, behind only taxi firms (65 attacks) but ahead of grocers (53). While gambling sites are obvious targets due to the large sums that accounts can contain, the grocers’ profile got a boost this year due to skittish customers filling their carts online during pandemic lockdown.
Over half (52%) of gambling operators reported a significant rise in ‘serious’ account takeover attempts this year, again, thanks to the surge in online gambling activity as land-based options diminished due to COVID-19.
Gambling operators led the way in citing ‘shared industry data’ as one of the most important factors when it comes to identifying fraud trends. Over half (56%) of gambling operators ranked shared data among their top three factors, while 20% listed it as the top factor. Other sectors were far more likely to cite customer profiles, order content, location and device ID as the top factor.
Ravelin CIO Mairtin O’Riada said blame for the havoc wrought by account takeovers was usually equally assignable to customers, merchants and banks, “but whenever it’s unclear, the merchant often takes the hit.”
Interestingly, the ‘digital goods’ sector, into which gambling is lumped, was the most likely to offer two-factor authorization (2FA) but customers were required to opt-in. Digital goods operators were among the lowest sectors in terms of enforcing 2FA for all users. Riada said 2FA was an effective means of mitigating takeover attempts, “but it can often be bypassed.”
That’s in part due to customers choosing some truly lame passwords that can be easily exposed by software dedicated to cracking such codes. Customers can exacerbate the situation by using the same lame passwords across multiple digital accounts.
The annual most popular online password list published by proprietary password managers NordPass shows ‘123456’ was the most popular password this year, dethroning 2019’s champ ‘12345’, which sank to eighth spot, while the super-literal ‘password’ ranked fourth. All of the above take less than a second to crack for anyone with the right tools.
If it wasn’t already obvious, security experts strongly urge the use of complex passwords involving a mix of alpha (upper and lower case) and numeric characters, along with special characters. Lengthier passwords are also considered much safer than shorter combos, and even those should be changed frequently.