Why are some*.Gov.PH websites redirecting users to gambling sites?
Here’s the thing. You did a Google search for some Gov.PH site information. But then, Google results could return search results with links like these below:
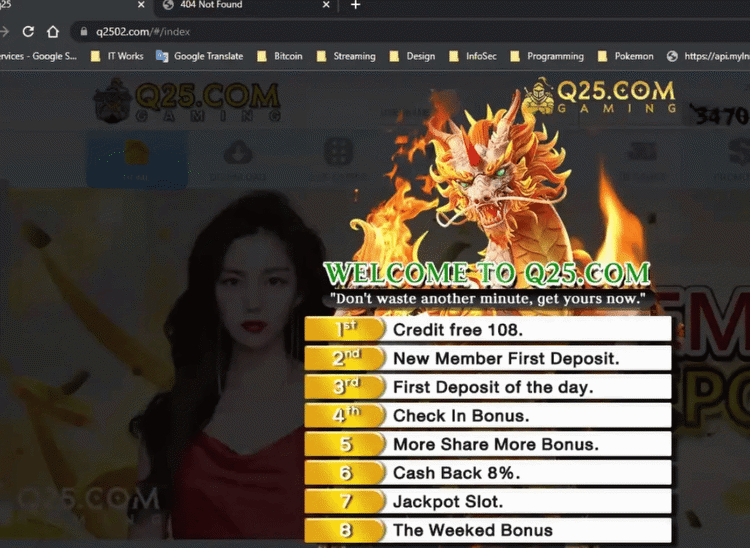
Since the site is a Gov.ph and the results come from Google, you wouldn’t be blamed for assuming that it is safe. So, you click on the circled link BUT you get to a gambling site instead!
How it all started
Eskie Maquilang, penetration testing engineer, KPMG first discovered this shocking tactic. Note: He did this in his personal capacity and as support to common friends.
Eskie noticed that hackers were triggering a lot of 403 errors (forbidden) on monitored servers. What got his attention were these URLs (uniform resource locators):
Now, why would hackers be searching for these specific files? Eskie thinks that the hackers are trying to confirm the presence of these files on your webserver. If these files existed on YOUR server/s, it meant that it was already compromised.
They or other hackers already uploaded the files via vulnerable plugins. And once the files are in your webserver, Google spiders/bots will index them. And once in the index, any search that matches it will be “served” by Google.
So how do all these files lead to gambling? These spuriously uploaded files contain the code that redirects web visitors to the hackers’ preferred sites. It also checks for the referrer link. This check will ensures that the links only work if the referrer is from Google.com or Bing.com! It doesn’t work with Duck Duck Go (score one for DDG!) The links to gambling sites won’t work if you type it in directly too.
Why is this dangerous?
Imagine that the hackers decided to redirect web visitors to FAKE gov.ph sites, or to Banking sites. PH users could be tricked into submitting sensitive information, or clicking on links simply because the link is trusted, i.e. *.gov.ph. Once you click on a link with malware, and it gets installed, you are well on your way to getting ransomware!
So you can see how much damage these tactics can cause if the hackers decided to take it further.
Motivation for this tactic?
For now, Eskie thinks this is a “black hat” SEO (Search engine optimization) tactic. It aims to boost the rankings so these gambling sites show up higher in the Google Search engine results. Remember that links coming from Gov.ph sites are juicier in terms of SEO.
Black hat SEO practices are tactics that are used to manipulate search engine rankings in ways that violate the search engines’ terms of service. This is a form of spamming and is (supposedly) not allowed by search engines.
How to fix this?
Use Google dork technics to see if your website is in the search results for such links. If your site comes up, better find those files and delete them. If you plan to pursue legal actions, it is best to get a screenshot of the file, including the creation time. You may want to report this incident to DICT Cybercrime division. This can help to prevent others from falling victim to the same scam.
Next, you MUST plug the ‘hole’ or the vulnerability that was used to get the files there in the first place. Some of the steps you can take to fix this file upload vulnerability in WordPress:
- Update WordPress to the latest version: WordPress regularly releases updates that include security fixes. Make sure that you are running the latest version of WordPress to protect against known vulnerabilities.
- Install a security plugin: There are many security plugins available for WordPress that can help protect against file upload vulnerabilities. Some popular options include Wordfence and Sucuri Security. These plugins can help to block malicious file uploads and alert you if any suspicious activity is detected on your site.
- Use strict file upload validation: When allowing users to upload files to your WordPress site, make sure to validate the files to ensure that they are safe. This can be done by checking the file type, size, and content of the uploaded file. You can use WordPress functions like wp_check_filetype() and wp_check_file_size() to do this.
- Use a dedicated file upload folder: Instead of allowing users to upload files to any location on your site, create a dedicated folder for file uploads. This will help to prevent users from uploading malicious files to important areas of your site.
- Use a secure hosting provider: Your hosting provider plays a key role in the security of your WordPress site. Make sure to choose a hosting provider that has strong security measures in place to protect against file upload vulnerabilities and other types of attacks.
Finally, please enable WAF! (Web Application Firewall). WAF automatically screens web requests and filters out likely attacks on your webserver. As always, I love hearing from you, do share your insights on this.
2022-12-31 09:46:00
["tech-news","technology","technology"]
[3156100,3156040,3156032,3156021,3155352,3155704,3155597]